Security researchers have created a clone of the Apple AirTag, to prove that the device and the anti-tracking features of the Find My network can be bypassed by hackers.

Since its launch, the tiny device advertised by Apple as a tracking device has been used by bad actors to spy on others and steal. While Apple has pre-installed features to limit usage that way, they’re mostly useless.
Following criticism of the threat posed by AirTag, on February 10, Apple said it would introduce a number of changes to the Find My network to address users’ fear of being tracked by AirTag.
However, security researcher Fabian Braunlein of Positive Security company said that the current and upcoming protections announced by Apple still have conspicuous holes, allowing bad guys to easily bypass them. Braunlein believes the flaw he found can be applied in practice.

The prototype version of the clone is quite large in size
To test the hypothesis, an AirTag “clone” was created by Braunlein. This AirTag “stealth” with all of Apple’s methods, can track iPhone users for more than 5 days without triggering any tracking notifications. Remember, iPhone users are favored by Apple with much more advanced anti-tracking measures than Android.
The researcher presented evidence that many elements of Apple’s change plan can be bypassed, starting with Apple’s claim that every AirTag has a unique serial number paired with Apple ID.
The AirTag clone doesn’t use the AirTag serial number and it’s not paired with an Apple ID, but still uses Apple’s Find My network.
While Apple is reducing the wait time before the AirTag alarms if detached from a paired Apple device, from more than 3 days to between 8 and 24 hours, the AirTag clone copes by not having a speaker. In fact, there are already speaker-disabled AirTags sold online.
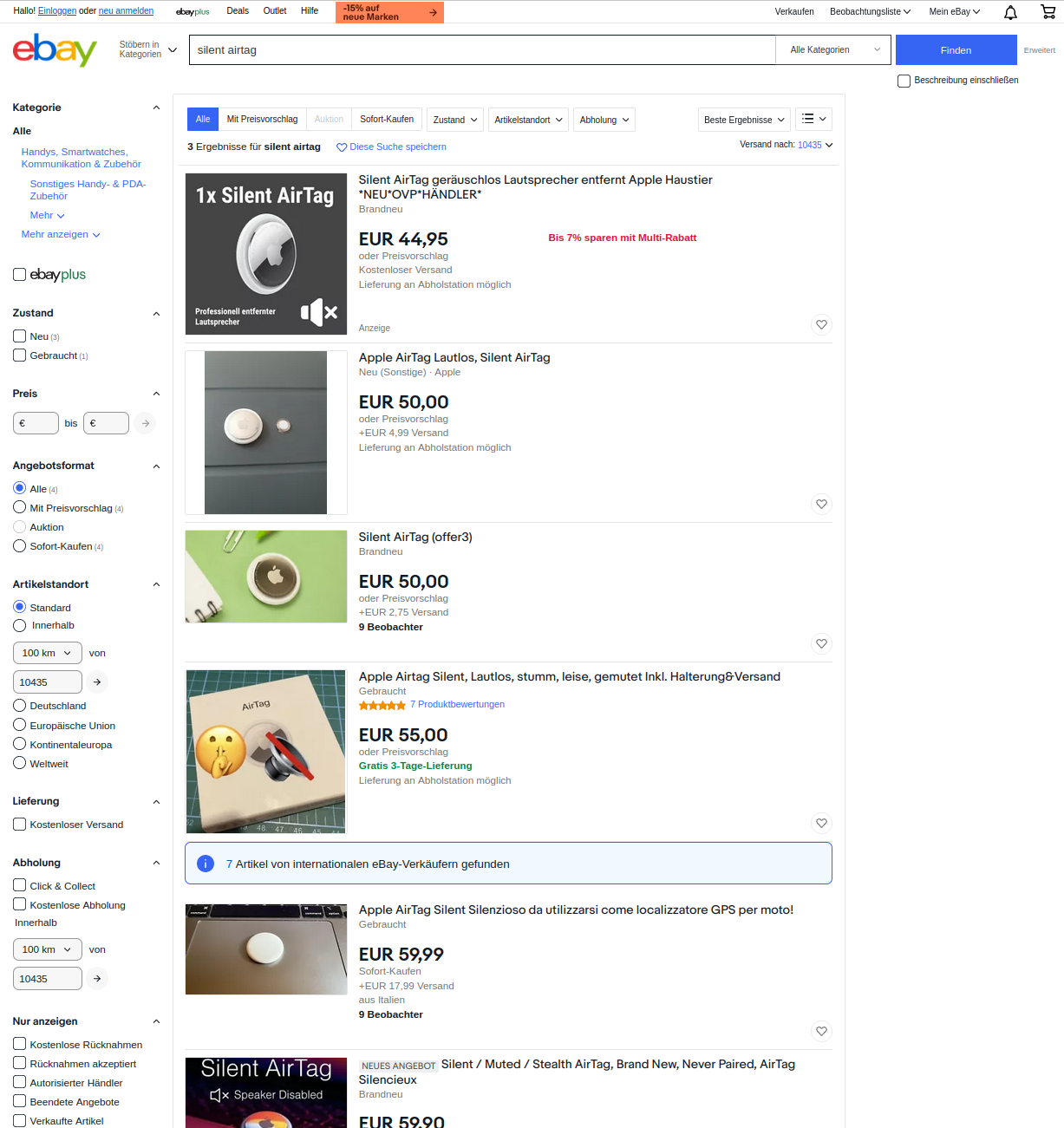
AirTag disables speakers sold online
Regarding the notice that Apple will send to the iPhone when it suspects that the user is being tracked by AirTag, Braunlein said that Apple’s method has a big flaw.
While Apple wants the AirTag to be undetectable by others over Bluetooth to avoid revealing information, the company also wants to be able to identify a specific AirTag to distinguish between a tag that goes with the owner and one that belongs to someone else. strange merely passing by.
Taking advantage of this, Braunlein solved it by installing more than 2,000 public keys (public encryption) into the AirTag clone and having it broadcast a key every 30 seconds.
For upcoming changes, items such as privacy warnings during setup and updated support documentation are considered unrelated to the clone version. The Precision Finding by Ultra Wideband feature is also not mentioned, as the microcontroller does not include a UWB chip, so cannot be found that way.
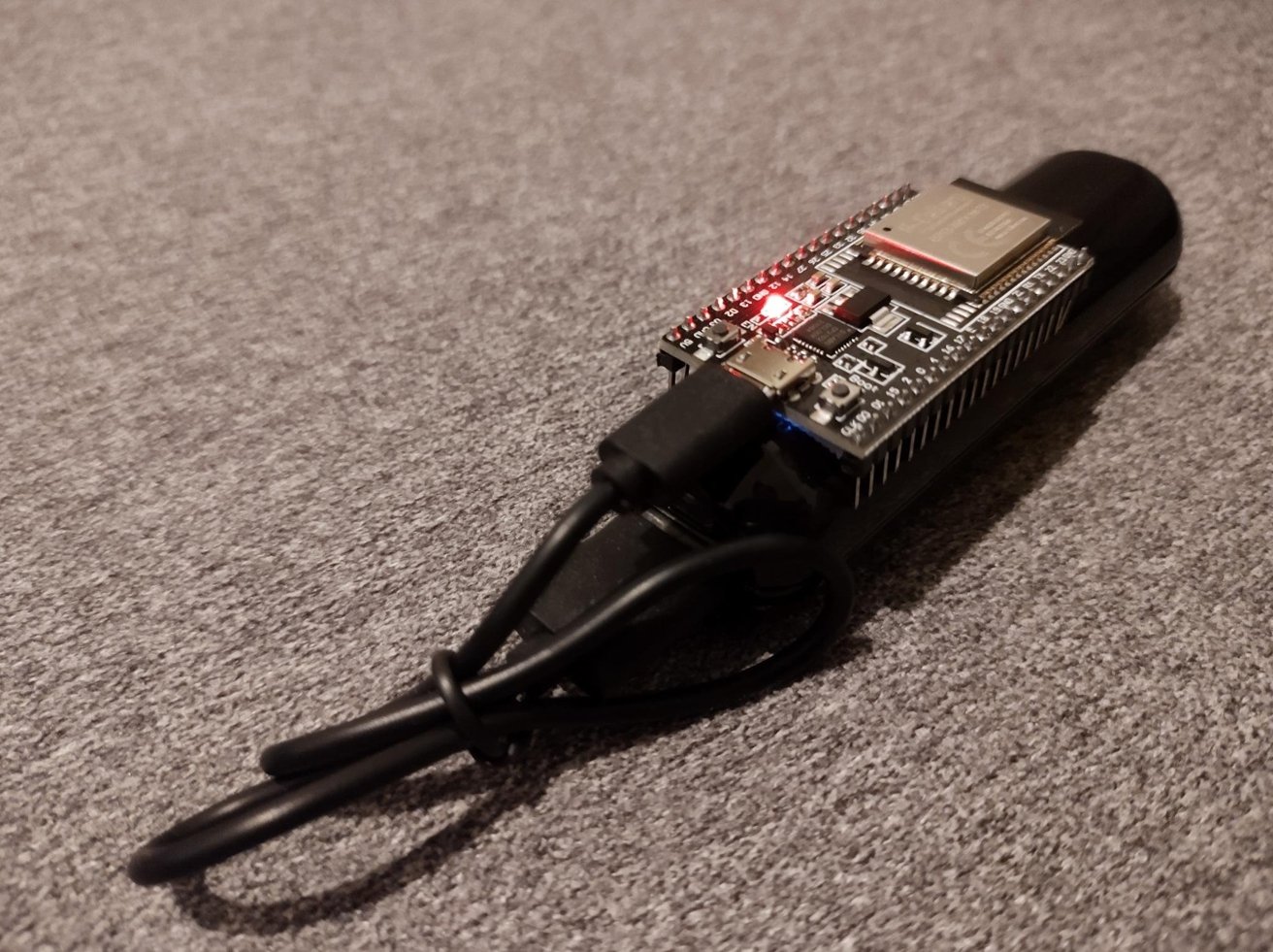
The version that Braunlein used during actual testing is quite compact, providing tracking capabilities based on Apple’s Find My network.
To create the AirTag clone, Braunlein used the system on OpenHaystack, a framework for tracking Bluetooth devices using the Find My network. Using an ESP32 microcontroller with Bluetooth support, a power bank and a cable, an AirTag clone was created.
AirTag clone used custom ESP32 firmware to constantly change the public keys, the list repeating about every 17 hours. However, an algorithm used on the AirTag clone and the Mac app used to track it was able to generate a “virtual key stream that never repeats”. Even if the police or Apple were able to get hold of the AirTag clone, it would be difficult to access the issued public keys.
During testing, Apple’s Android Tracker Detect app did not display the AirTag clone tag at all. AirGuard, an Android app that can be used to scan nearby Find My devices created by TU Darmstadt labs, can detect the AirTag clone, but it shows up as multiple devices due to the public key changed. change.

Apple’s Android Tracker Detect app doesn’t show the AirTag clone tag at all
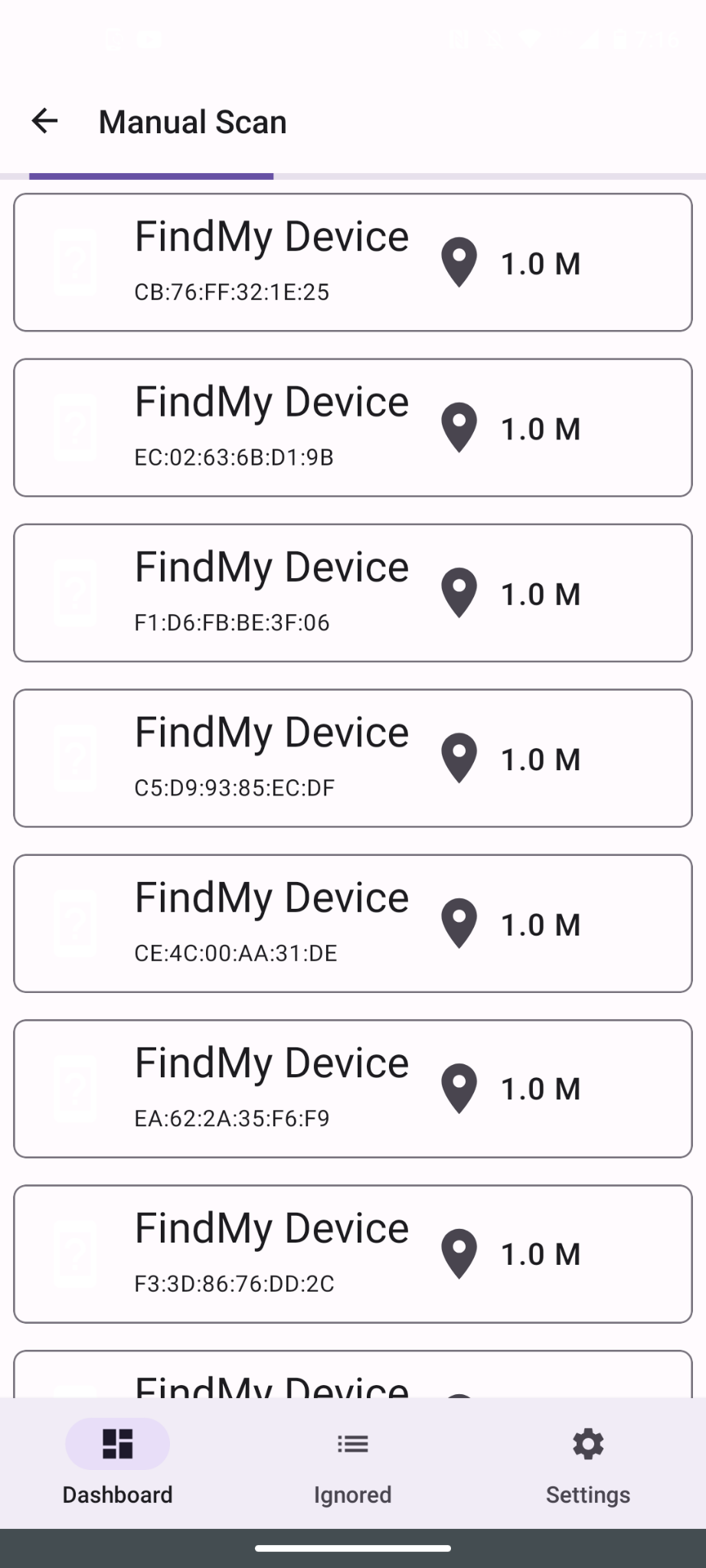
AirTag clones show up as multiple devices in AirGuard
The researcher claims to have successfully tracked an iPhone user for 5 days (with their consent to participate in the test) without triggering a single tracking notification, nor did his roommates using the iPhone. see notification.
Summing up the testing process, Braunlein believes that the main risk lies not with the AirTags themselves but with the advent of the Find My ecosystem that uses customers’ devices to provide services. Braunlein thinks Apple should consider increasing the security of this network.
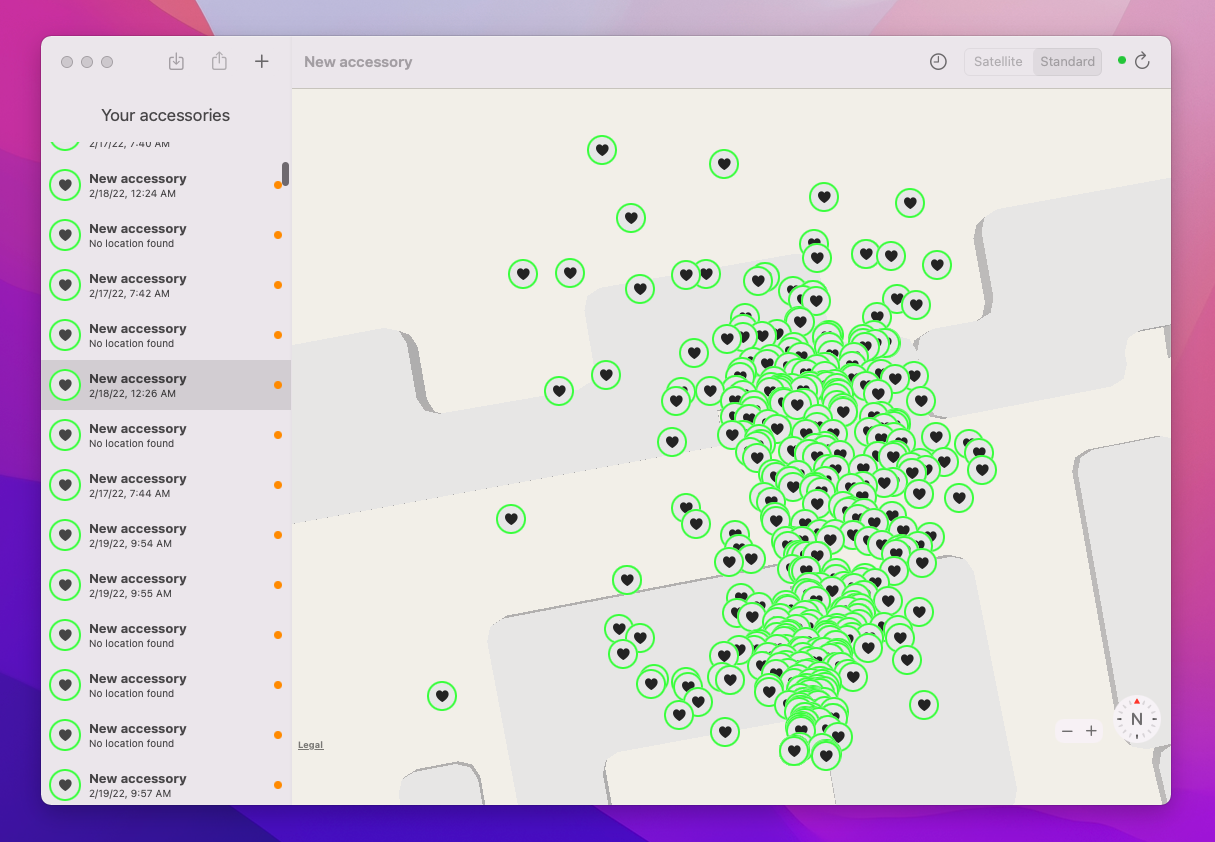
macOS app used to track AirTag clone
Braunlein said: “They need to account for the potential dangers of making homemade, using Find My or AirTag protocols with modified hardware. With a spare battery and ESP32 cheaper than AirTag, this could be the impetus for some. creator instead of using AirTag.”
The researcher concluded: “We do not encourage abuse of this method, we hope that sharing this experiment will bring about positive changes to the security and privacy of the Find My ecosystem.”
Reference: AppleInsider
