According to Check Point security researchers, six malicious apps were downloaded 15,000 times before Google removed them from the store thanks to the warning. It is worth noting that these applications disguise themselves as anti-virus apps, but they are accompanied by Sharkbot malware that steals users’ passwords.
Sharkbot works by tricking victims into entering their credentials into fake windows, which often appear when malware detects banking applications are open. It can also steal information by keylog (keyboard tracking), intercept SMS messages and gain full remote access.
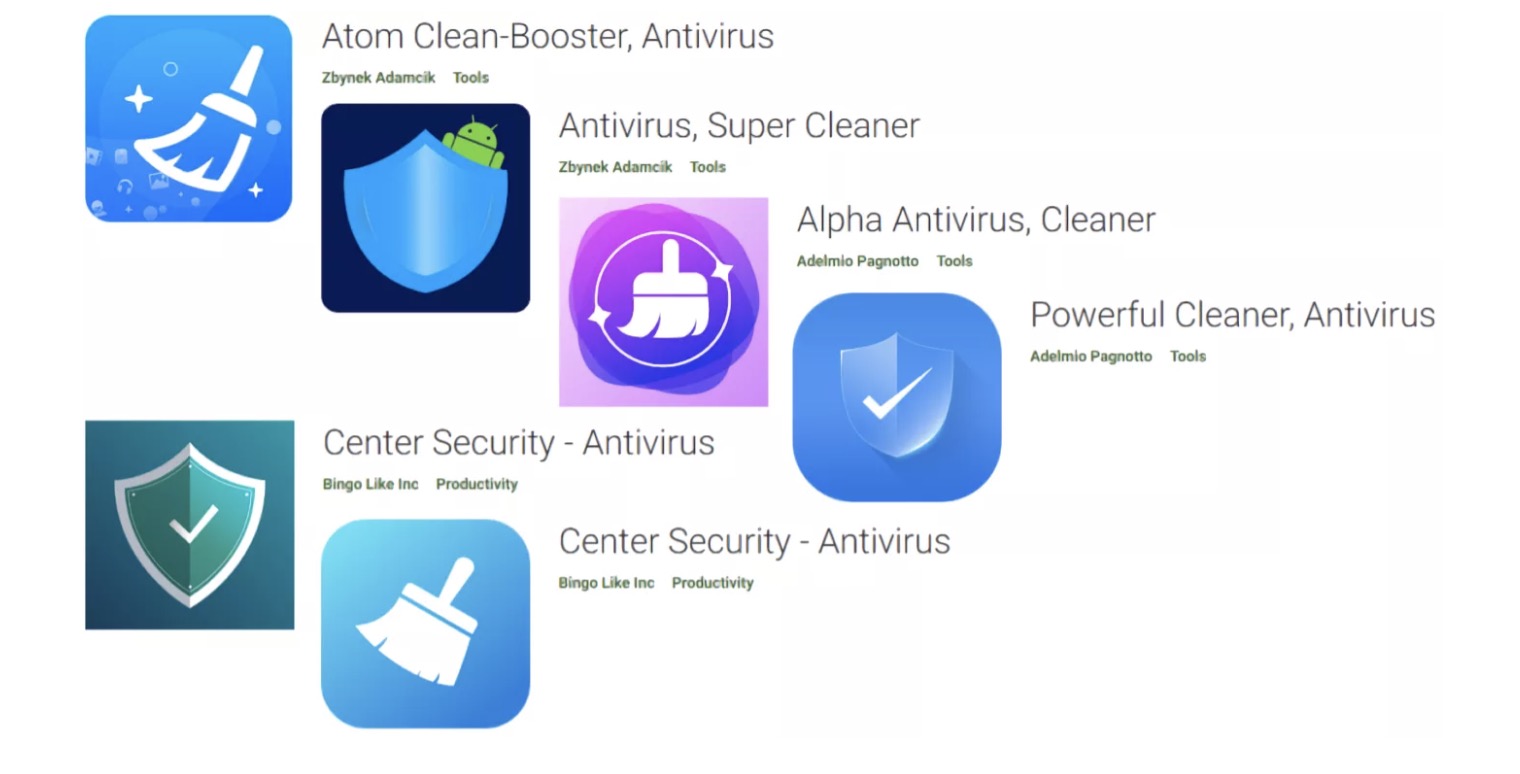
After the victim enters their username and password, the details are sent to the malware’s server and used by the bad guys to access bank accounts, social networks, emails, etc.
The malware mainly targets victims in the UK and Italy. It is capable of using geolocation to identify and bypass users in China, India, Romania, Russia, Ukraine or Belarus.
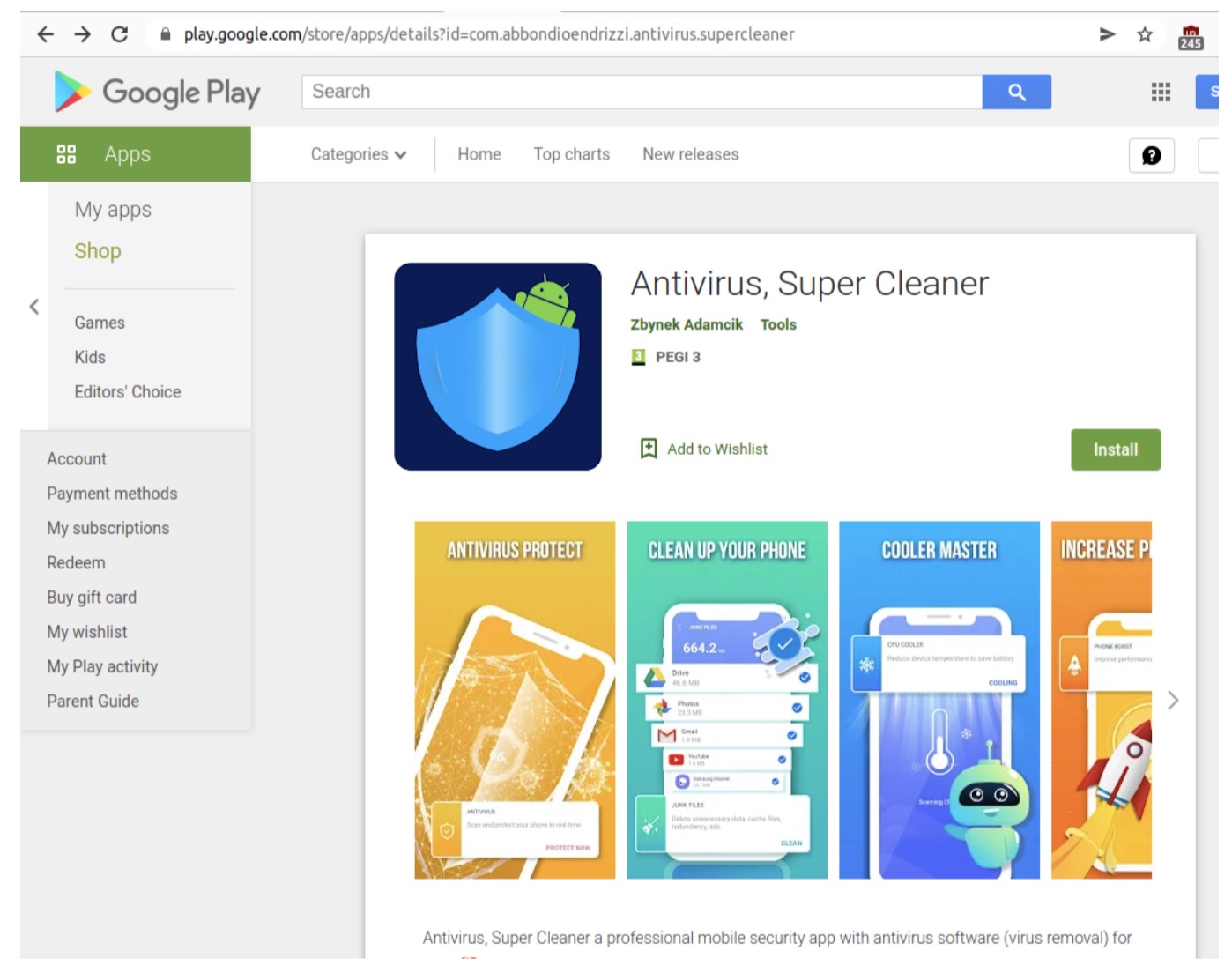
Apps can bypass Play Store protections because their malicious behavior isn’t triggered until someone downloads them and they have a chance to communicate with the server.
Apps containing Sharkbot were removed from the Google Play Store in March, but they are likely still available on third-party stores.
Reference: ZDNet
