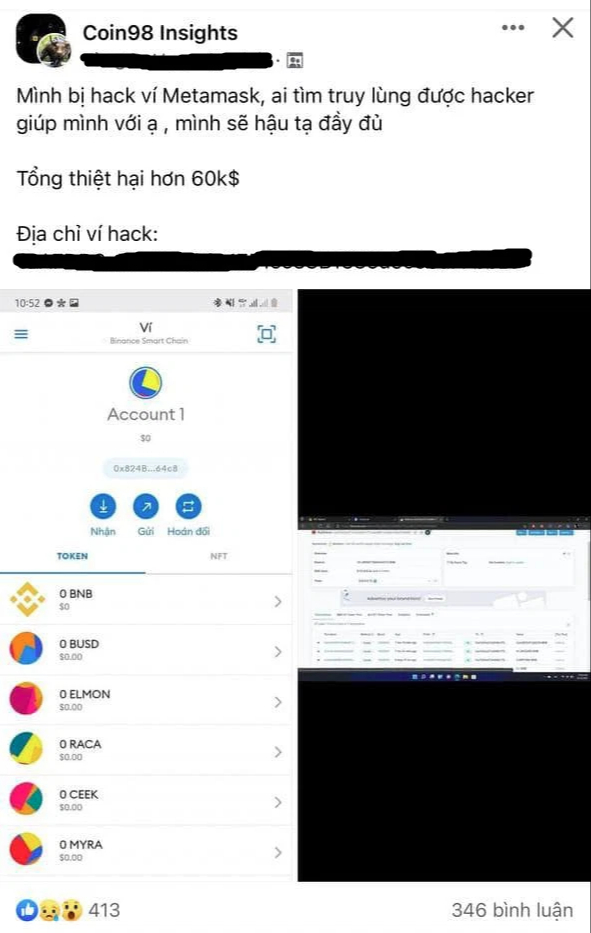
Along with the exciting cryptocurrency market, the theft of users’ virtual currency is also becoming more and more common. It is worth noting that it often happens with decentralized electronic wallets (non-custodial wallets) such as Metamask, C98, Ronin, … , where users own their own keys and have full discretion with property in it. It is different from the e-wallet used on cryptocurrency exchanges.
Because this type of wallet exists independently of exchanges, even if an exchange is hacked, users are still not affected. Therefore, if the assets in this wallet of a user are stolen, the possibility of recovering it is also very low. But no matter how complicated the passwords are devised by users, it is a fact that hackers can easily get through and rob your wallet.
But according to security expert Le Nguyen Khang, the problem is not with the difficulty of the password you set for your wallet, but with the device you use to store the password and how you use it. any.
A common habit of many users is to install those e-wallets into the browser, especially Google Chrome, to facilitate use on many different devices, as well as pay for different services on the Internet. cryptocurrency market.
To access this wallet on different devices, users will need 2 types of private keys: a key that is generated by the wallet provider, such as Metamask, for the user, containing between 12 and 24 characters, in addition to the key. In addition, there is another type of key that is set by the user. With many types of encryption today, users often have the habit of storing this key information in a text file right on the user’s device.
These many layers of protection will make you completely secure in trading digital currencies on the internet, but according to Mr. Khang, hackers have many ways to get the information to protect your account and get rid of the assets in it. . It is a bruteforce attack on the browser to see the passwords stored in it, bypassing this step, the hacker begins to put a foot in your e-wallet.
In addition, currently hackers in the cryptocurrency world have written malware that specializes in scouring data files, e-wallet log files, browser login information, text files stored on the Desktop. or the Documents folder on your computer. These are also the two places where users often place text files that store the character string of the key that the e-wallet provider provides to the user.
With the collected malware data, hackers can scan and find this key sequence, even the password stored in it, from which to bruteforce the correct key and password to log in to the e-wallet on the browser. .
In addition, many people also have the habit of using one password or setting a password (eg Abc123, Abc345, …) for many different online accounts, so when bruteforce to find out the key, the password can be viewed. If the password is stored in the browser, the hacker can guess the private key that the user sets for the wallet account, if they do not save it together in a text file with the above 12-character key chain.
More ominously, according to Mr. Khang, this type of malware works on multiple platforms, so whether you are using Windows, MacOS or Linux, you are likely to become a victim of hackers.

That’s not to mention many cases of users installing pirated computer software or malicious browser extensions. These malicious codes make it easier for hackers to access the important data you store on it, as well as pave the way for hackers to enter your e-wallet.
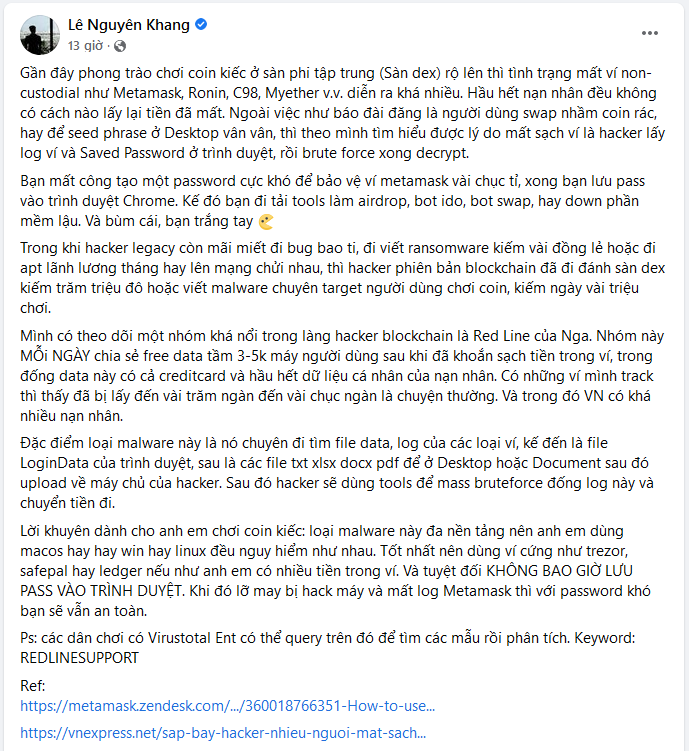
According to Mr. Khang, the above seemingly complicated process of breaking the lock is causing unimaginable damage to many people. A fairly well-known group of hackers in the blockchain industry is Russia’s Red Line that can EVERY DAY freely share data containing between 3,000 and 5,000 user computers – all of which have been hacked and wiped out their e-wallets. Many victims have been taken from tens of thousands of dollars to hundreds of thousands of dollars. There are also many victims from Vietnam.
Although users themselves are always vigilant, but because the user’s computer is a place where hackers can easily infiltrate and search for data, according to Mr. Khang, NEVER SAVE PASSWORD INTO THE Browser. If you do this, if you are accidentally hacked into your computer by a hacker, you are still safer from attacks.
.
